Old tools
Panasonic RW2 files lens distortion correction information
Panasonic includes lens distortion correction data in their RAW files as an EXIF tag. Unfortunately, they did not release the specification for this tag. Which is really annoying for people willing to use a RAW converter which is not vetted by Panasonic.
Inspired by this blog post : Dissecting Panasonic RW2 files.
I decided to take the plunge and finally find out
what's behind the format.
The following command allows us to get the raw
hex bytes of the 0x119 tag, which includes the correction data :
The data is only 32 bytes long, which should make it quite easy to parse.
After some (err a lot of) reverse engineering work, I finally understand enough
to write a parser : the data is infact 16 short (16 bits) integers, represented
in little endian order :
Words 0, 1, 14 and 15 are checksums, see the code for the algorithm.
Word 7 is a flag : 0 means the distortion correction data shouldn't be applied,
1 means it should. Other values seem to be invalid
The rest seems to represent 2 types of data, but only one seems to be used, consisting of words 12, 5, 8, 4 and 11. Changing words 2, 3, 6, 9, 10 and 13 doesn't seem to have any effect.
- word 12 seems to be always be equal to 2500, changing it disables distortion correction
- words 5, 8, 4 and 11 are floating point numbers encoded as signed
integers. Divide them by 32768 to get the original value.
- Word 5 is a scale factor.
- Word 8 is the primary (a) coefficient for the distortion correction
- Word 4 is the second (b) coefficient for the distortion correction
- Word 11 is the third (c) coefficient for the distortion correction
This can be summarized by :
n = data[12]; scale = 1.0/(1.0+(data[5]/32768.0)); a = data[8]/32768.0; b = data[4]/32768.0; c = data[11]/32768.0;Now after playing with Adobe DNG Converter to get a clue on the equation used, it seemed parameters a b and c roughly match the following equation :
Ru = scale*(Rd + a*Rd^3 + b*Rd^5 + c*Rd^7)Reversing SilkyPix confirms it. But it computes it in a weird way :
double table[100]; for(i=0; i<100; i++) table[i] = f(i/25.0); And stops computing if the derivative becomes negative or if the value exceeds 2.
Unfortunately, more tests with lensfun got me confused, and for
example, trying the "poly3" model gives completely different results.
You can find below some tools which helped me reverse engineer the
format, including the code to fix checksums.
Please check Andrew Johnston's work on the subject : http://www.andrewj.com/mft/
TODO
Tag 0x011b contains information to correct chromatic aberrations.
History
- 30/04/2011 : 0.1 : first public release
Download it here : panarw2-v0.1.tar
Windows, with binaries : panarw2-0.1.zip
Github : https://github.com/trou/panasonic-rw2
AirScan : a Nintendo DS Wi-Fi access point scanner
AirScan is a Wi-Fi scanning utility for the Nintendo DS. It offers various
filtering features to facilitate access point discovery.
For example, it can be used to locate open access points in low WiFi density
areas thanks to its sensivity.
Interesting features include :
- Display only desired protection levels (open, WEP, WPA)
- Connectivity testing for open access points (including retrieval of the Google homepage)
- Easy scrolling
- Timeouts for out of range APs
Screenshot
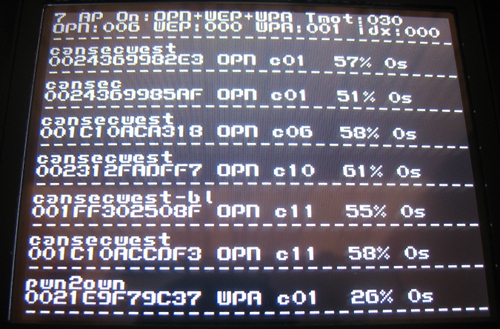
History
- 07/11/2010 : 1.0 : improved connectivity testing, new icon
- 20/02/2010 : 0.6 : fix for scrolling and timeouts
- 18/01/2010 : 0.5.1: mode selection bugfix
- 09/01/2010 : 0.5 : connectivity testing, many bugfixes
- 02/03/2009 : 0.2 : timeouts
- 26/06/2008 : 0.1a : first public release
Download
Download it here : airscan-v1.0.zip
Github
You can find the code on GitHub too : https://github.com/trou/airscan.MIPS (MIPS IDA PluginS)
IDA, until version 5.5, didn't understand the so-called "old abi" of MIPS ELF binaries.
I wrote this IDAPython plugin which parses the ELF itself to resolve calls to external libraries.
It also handles switch tables and internal symbols. It helps a LOT while reversing embedded binaries.
It is partially based on the work of Julien Tinnes : mips.elf.external.resolution.txt.
It also includes two little Python scripts (ident_func.py and ident_func_le.py) to identify all functions in a binary, which helps a lot for cross references.
Screenshot
Usage
- Read the documentation on top of the source
- (optional) run ident_func.py
- Run the plugin in IDAPython, it will ask if you want to analyze the whole segment or just the current function
- Click "yes" or "no"
- Enjoy !
History
- 26/02/2009 : 1.5.3 : Bugfix in switch table parsing (thx to the reporter)
- 18/09/2008 : 1.5.2 : Bugfix + ident_func_le.py
- 06/09/2008 : 1.5.1 : First public release
Download
Download it here: mips-analyser-1.5.3.zipMBSA Extractor
MBSA is a tool from Microsoft used to verify if your systems
are up-to-date.
My tool uses MBSA's database to download specific updates, extract them, sort them on the disk, etc.
It can be very useful to download several versions of the same file.
Usage
The tool has been designed for flexibility and updates can be selected using many criterias : Some valid search expressions : CVE=CVE-2006-1234 SID=date(20041225,20060101) KBID=147258 xpath='//Update[./ExtendedProperties/SecurityBulletinID[text()='MS06-040']]'History
- 15/10/2008 : 1.0 : First public release
Download
You'll need the ruby-xml-smart library : http://raa.ruby-lang.org/project/ruby-xml-smart/.Download it here: mbsa-1.0.tar.bz2
Debian OpenSSL vulnerability
We (Raphaël Rigo, Romain Raboin and Julien Tinnes) gave a short talk at SSTIC 08 about some of the tools we wrote after the OpenSSL/Debian advisory to remotely discover vulnerable keys in authorized_keys files, decipher SSH traffic and retrieve DSA private keys (even from non weak keys). We also wrote an article in french in this MISC issue.
The main page for those tools is there but you can find my tools (written with Yoann Guillot) to decrypt vulnerable OpenSSH session captures on Yoann's Github :https://github.com/jjyg/ssh_decoder and the keygen tool here : https://github.com/trou/ssh_key_keygen or here : ssh_kex_keygen-1.1.tar.bz2.Various stuff
If no licence is specified, consider it's GPL v3.